Progressive loading of Timeline for massive data
Timeout in Spider on production data :(
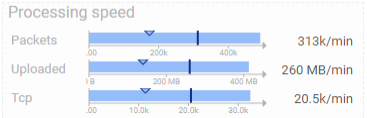
In Flowbird production environment, Spider is capturing around 400GB per day. Impressive!
But it is a challenge by itself! If the capture works great, the UI, map and statistics are getting timeouts when loading the timeline around the whole day.
Progressive loading with composite aggregation
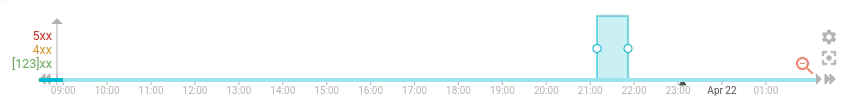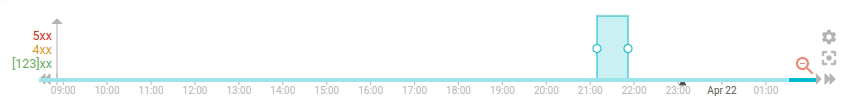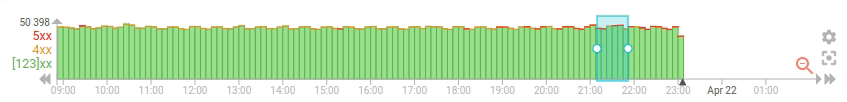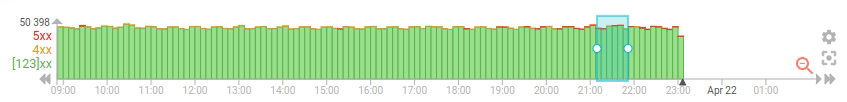
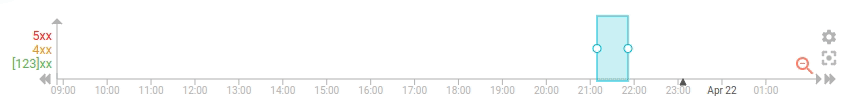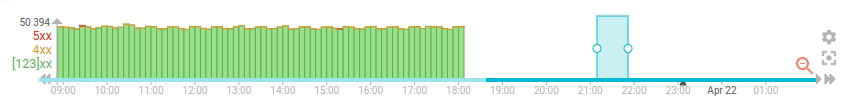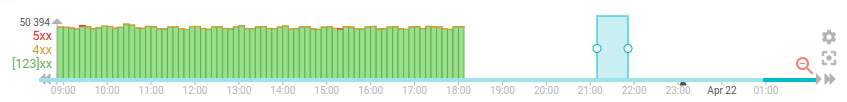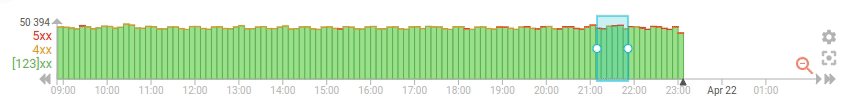
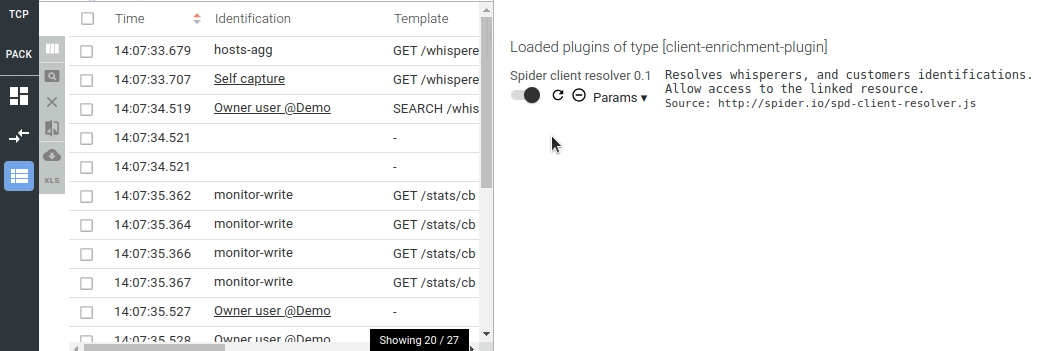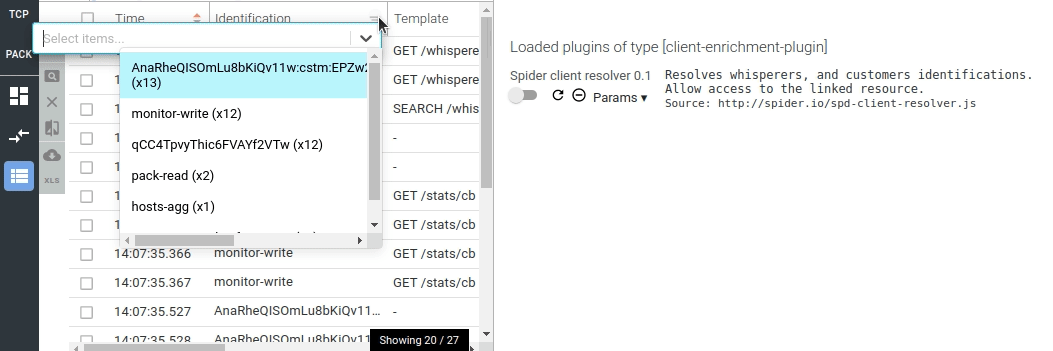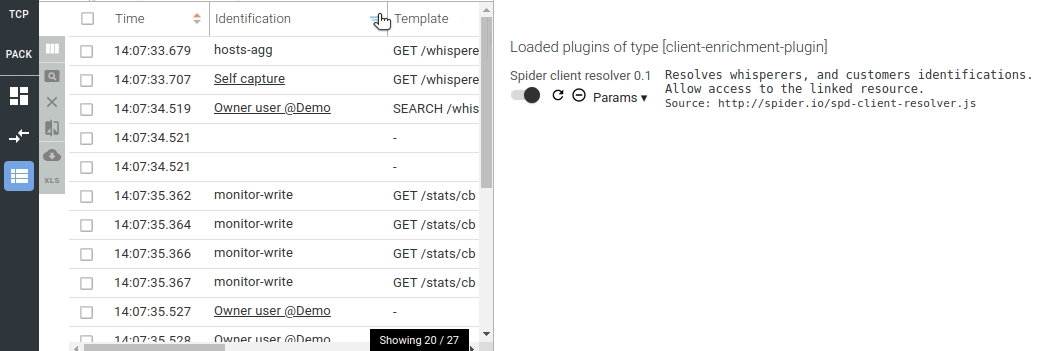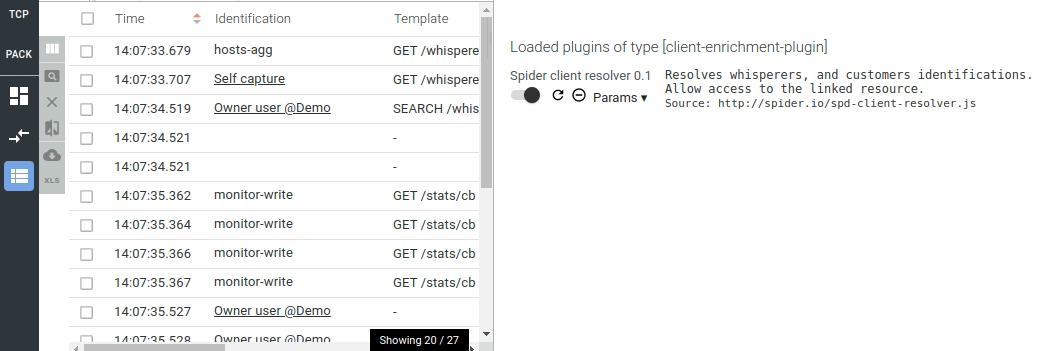
To improve the situation, I've added an option to the timeline (first) to do progressive loading of the data, with pagination. It uses the composite aggregation of Elasticsearch, and the results is updated the existing timeline data whenever possible, instead of resetting the whole timeline everytime
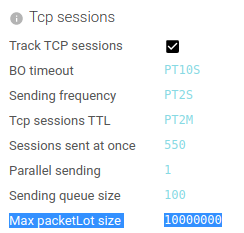
The settings is activated by default and may be deactivated in the display settings:
Result: Pros & Cons mix
Pros
- The progressive loading is really visible
- It makes cancelling the timeline loading expensive query quite easy
- It limits the load on the server when the user navigate quickly on the timeline
Drawback:
- Loading the timeline data gets longer. Pagination implies many requests made to the server in sequence, with a request overhead for each call.
I think it is worth it.